Proposed protocol simulation in presence of the intruder.
Par un écrivain mystérieux
Description

Secure intrusion detection system routing protocol for mobile ad

RPL network with HELLO flood attack after 10 minutes of simulation

Distributed Authentication Security for IOT Using DASS and LOKI91
ISEND: An Improved Secure Neighbor Discovery Protocol for Wireless

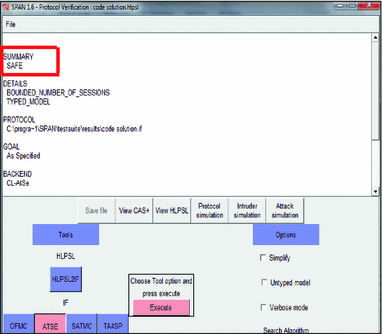
Intruder simulation of case 2 in AVISPA using CL-AtSe
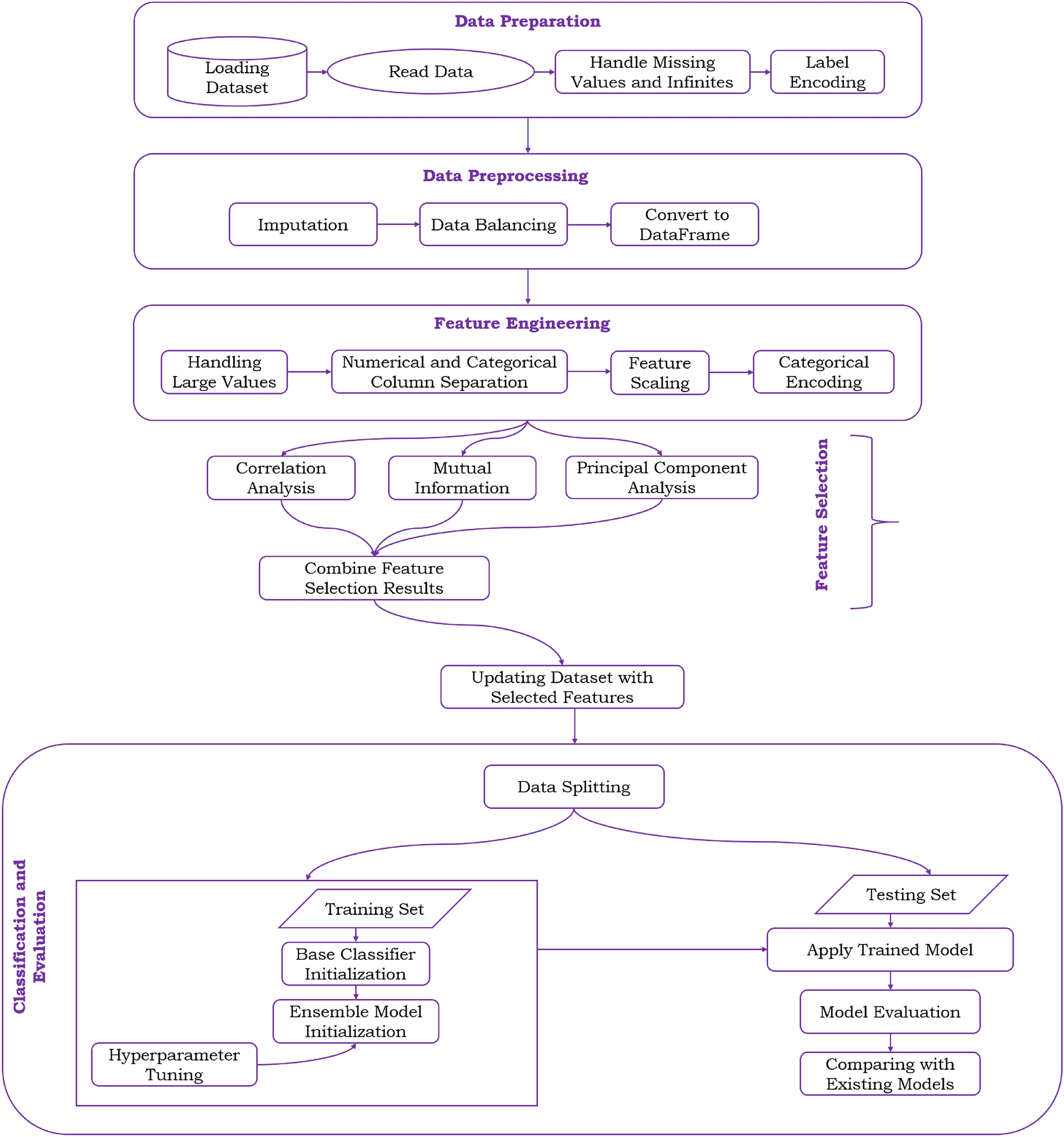
A novel hybrid feature selection and ensemble-based machine

Mathematics, Free Full-Text

Basic animation with the intruder, the intruder may take advantage

Full article: Securing the cyber-physical system: a review

Intruder simulation of case 1 in AVISPA using CL-AtSe

Machine learning and smart card based two-factor authentication

Analysing Security Protocols Using Scenario Based Simulation
depuis
par adulte (le prix varie selon la taille du groupe)